Our Expertise
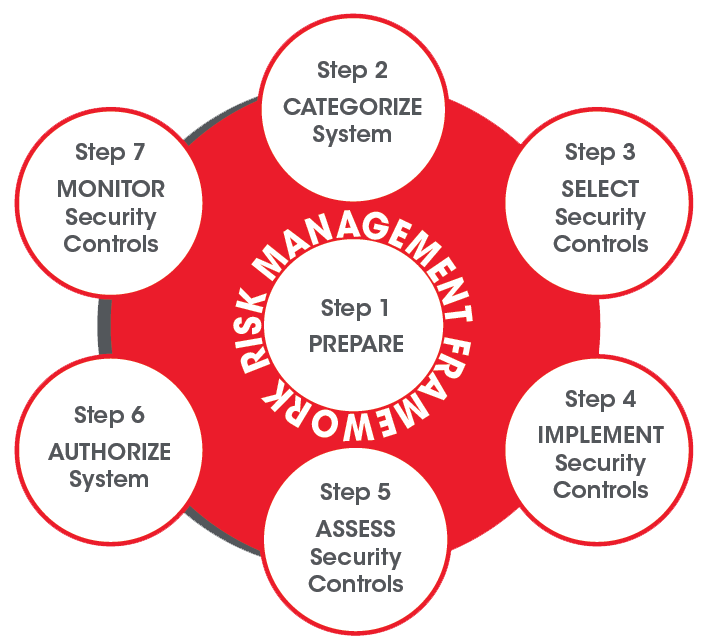
Are your information systems or cybersecurity programs still operating under DIACAP? Do you need to become compliant with Risk Management Framework (RMF) 2.0? RMF is a seven-step process that incorporates standards used by federal agencies and the DOD community to make informed, risk-based decisions regarding security policies and controls. Through tailored documentation, stakeholder engagement, and a customized approach to meet your business needs, H2L Solutions streamlines the migration process to RMF.
Categorization Guidance & SSP Development
Following Federal Information Processing Standards (FIPS) and the National Industrial Security Program Operating Manual (NISPOM), and utilizing interviews, H2L Solutions facilitates determination by the customer of the criticality and sensitivity of information systems. Coordinate development of the System Security Plan (SSP) supporting artifacts summarizing security requirements for the organization and defining security controls.
Implementation Plan & Security Controls
Formalize your organization’s implementation plan, documenting security mechanisms, network designs, configuration changes, and contingency plans. Ensure security controls meet minimum baselines including necessary overlays, while addressing current threats. Hardware and software deployment services are tailored to meet business needs and streamline RMF compliance.
eMASS & SRG/STIG Support
Aid customer utilization of eMASS, the collaborative solution used to automate and manage process control mechanisms and report generation. Secure customers hardware and software through implementation of applicable Security Requirements Guides (SRGs) and Security Technical Implementation Guides (STIGs).
Risk Assessments & Controls Inspections
Using qualitative and quantitative methods, we will conduct risk assessments in the context of threats, vulnerabilities, likelihoods, and potential impacts. Pre-inspections are done to test security controls for effectiveness and compliance prior to third-party validation events. Penetration testing and vulnerability assessment services are also available.
POA&Ms & SAP Documents
Assist with Plans of Action and Milestones (POA&Ms) to define how your organization is going to address specific security concerns, including measures to correct deficiencies or non-compliant controls, and to reduce or eliminate vulnerabilities. Help with preparing the Security Authorization Package (SAP) containing all necessary information and artifacts submitted to the Authorizing Official.
POLICIES & ARTIFACTS
Support with writing policies for all 18 control families outlining security procedures or configurations used by your organization. Policies are written at the control correlation identifier (CCI) level to support control import into eMASS. H2L Solutions goes beyond compliance, ensuring effective risk-based security measures will work within your enterprise life cycle, protect your assets, and meet strategic objectives.